Using Postman: Difference between revisions
Jump to navigation
Jump to search
Email
No edit summary |
No edit summary |
||
| Line 27: | Line 27: | ||
# For auth: UserLevel, need to send '''“targerUserId”''' in Params>Path Variables> <p>KEY: targetUserId </p><p>VALUE: <targetUserId> | # For auth: UserLevel, need to send '''“targerUserId”''' in Params>Path Variables> <p>KEY: targetUserId </p><p>VALUE: <targetUserId> | ||
</p> | </p> | ||
=== Email === | === Email === | ||
| Line 64: | Line 65: | ||
==== example reloPermission ==== | ==== example reloPermission ==== | ||
*'''AppLevel:superUser''' | |||
<syntaxhighlight lang="JavaScript"> | <syntaxhighlight lang="JavaScript"> | ||
{ | { | ||
"roleIdKey":"AppLevel_this-is-uuid-role-superUserA", | "roleIdKey":"AppLevel_this-is-uuid-for-role-superUserA", | ||
"service_resource_action":" | "service_resource_action":"ServiceTemplate_Config_Create", | ||
"permission": "accept" | "permission": "accept" | ||
} | } | ||
</syntaxhighlight> | </syntaxhighlight> | ||
*'''AppLevel:verifiedUser''' | |||
<syntaxhighlight lang="JavaScript"> | |||
{ | |||
"roleIdKey": "AppLevel_this-is-uuid-for-role-verifiedUserA", | |||
"service_resource_action": "ServiceTemplate_Config_Create", | |||
"permission": "accept" | |||
} | |||
</syntaxhighlight> | |||
*'''AppLevel:basicUser''' | |||
<syntaxhighlight lang="JavaScript"> | |||
{ | |||
"roleIdKey": "AppLevel_this-is-uuid-for-role-basicUserA", | |||
"service_resource_action": "UserAccountAppLevel_UserRole_Get", | |||
"permission": "accept" | |||
} | |||
</syntaxhighlight> | |||
==== example UserRoles ==== | |||
*'''AppLevel:superUser''' | |||
<syntaxhighlight lang="JavaScript"> | |||
{ | |||
"userId": "this-is-uuid-for-user-superUserA", | |||
"roleIdKey": "AppLevel_this-is-uuid-for-role-superUserA" | |||
} | |||
</syntaxhighlight> | |||
*'''AppLevel:verifiedUser''' | |||
<syntaxhighlight lang="JavaScript"> | |||
{ | |||
"userId": "this-is-uuid-for-user-verifiedUserA", | |||
"roleIdKey": "AppLevel_this-is-uuid-for-role-verifiedUserA" | |||
} | |||
</syntaxhighlight> | |||
*'''AppLevel:basicUser''' | |||
<syntaxhighlight lang="JavaScript"> | |||
{ | |||
"userId": "this-is-uuid-for-user-basicUserA", | |||
"roleIdKey": "AppLevel_this-is-uuid-for-role-basicUserA" | |||
} | |||
</syntaxhighlight> | |||
==== setting for authorizer appLevel ==== | ==== setting for authorizer appLevel ==== | ||
| Line 88: | Line 130: | ||
resultTtlInSeconds: 0 | resultTtlInSeconds: 0 | ||
</syntaxhighlight> | </syntaxhighlight> | ||
| Line 105: | Line 146: | ||
==== example rolePermission ==== | ==== example rolePermission ==== | ||
* Create role permission, user can do action, can create in seed data or run from https://us-east-2.console.aws.amazon.com/apigateway/home?region=us-east-2#/apis/rwnhg855jd/resources/y8erkk : '''RolePermissionCreateHdrApi''' | * Create role permission, user can do action, can create in seed data or run from | ||
https://us-east-2.console.aws.amazon.com/apigateway/home?region=us-east-2#/apis/rwnhg855jd/resources/y8erkk : '''RolePermissionCreateHdrApi''' | |||
*'''UserLevel:verifiedUser''' | |||
:<syntaxhighlight lang="JavaScript"> | :<syntaxhighlight lang="JavaScript"> | ||
{ | { | ||
| Line 115: | Line 158: | ||
</syntaxhighlight> | </syntaxhighlight> | ||
* Create userRoles, user have role, can create from https://us-east-2.console.aws.amazon.com/apigateway/home?region=us-east-2#/apis/rwnhg855jd/resources/y8erkk : UserRolesCreateHdrApi | ==== example userRoles ==== | ||
* Create userRoles, user have role, can create from | |||
**https://us-east-2.console.aws.amazon.com/apigateway/home?region=us-east-2#/apis/rwnhg855jd/resources/y8erkk : UserRolesCreateHdrApi | |||
*'''UserLevel:verifiedUser''' | |||
:<syntaxhighlight lang="JavaScript"> | :<syntaxhighlight lang="JavaScript"> | ||
{ | { | ||
Revision as of 08:13, 10 October 2022
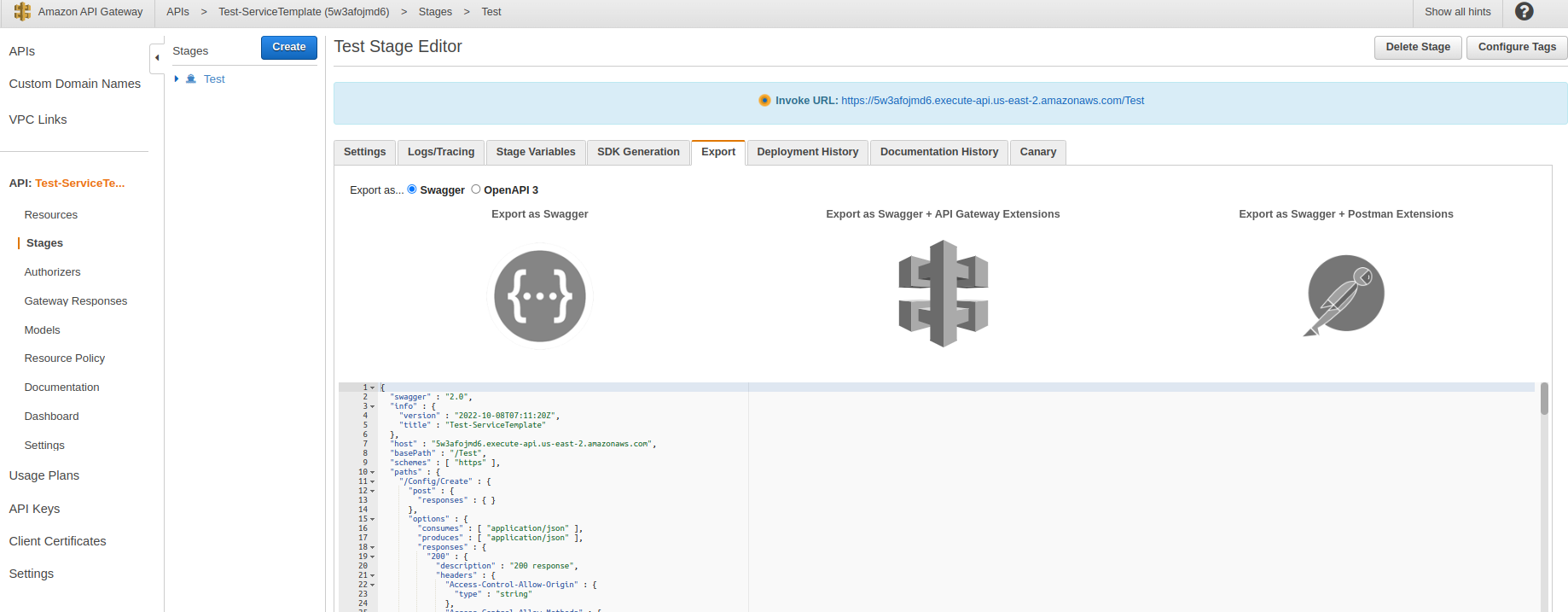
Connecting Postman to API Gateway
Connect API to Post man.
- AWS API Gateway: click name of service api
- Click stage /Test
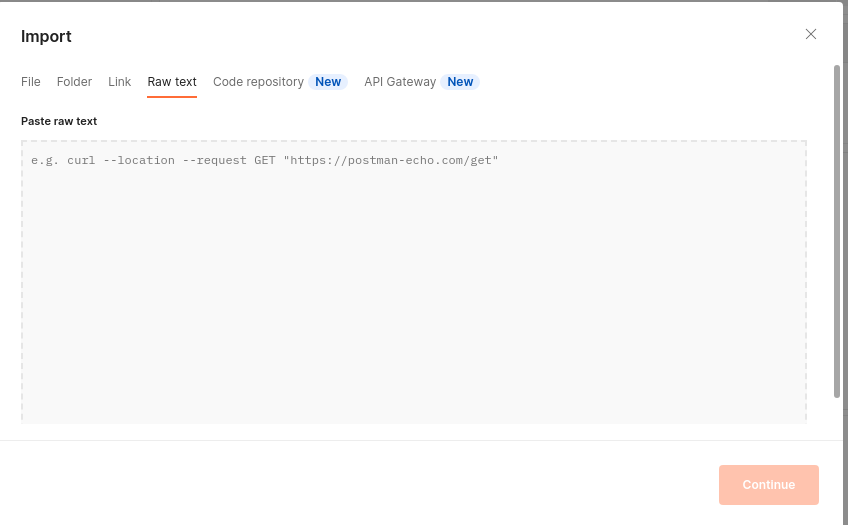
- and click export choose ..”Export as Swagger+Postman Extensions” copy code JSON
- Go to postman and paste in import/ Raw text/ continue.
- Now My Workspace connect to Api finished.
Access Token
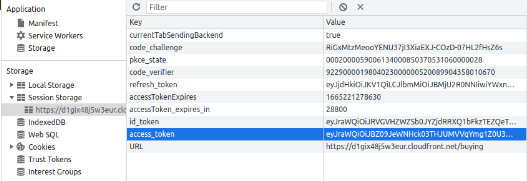
web interface: https://d1gix48j5w3eur.cloudfront.net/buying
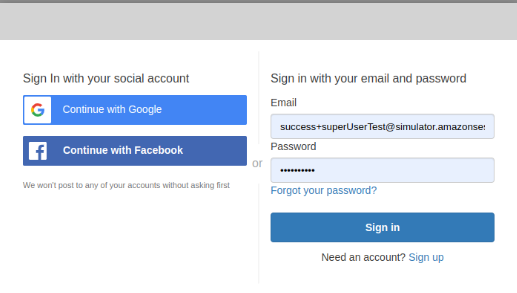
- Navbar > Sign in using mock account (suggested), if you signup with new user will get default role in basicUser, that mean you NOT allow to access all functions.
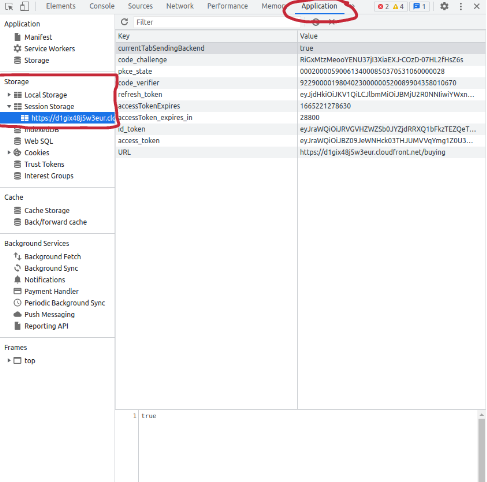
- F12 to see element
- select tab >> Application
- Session Storage > http... > access_token and copy these token to postman
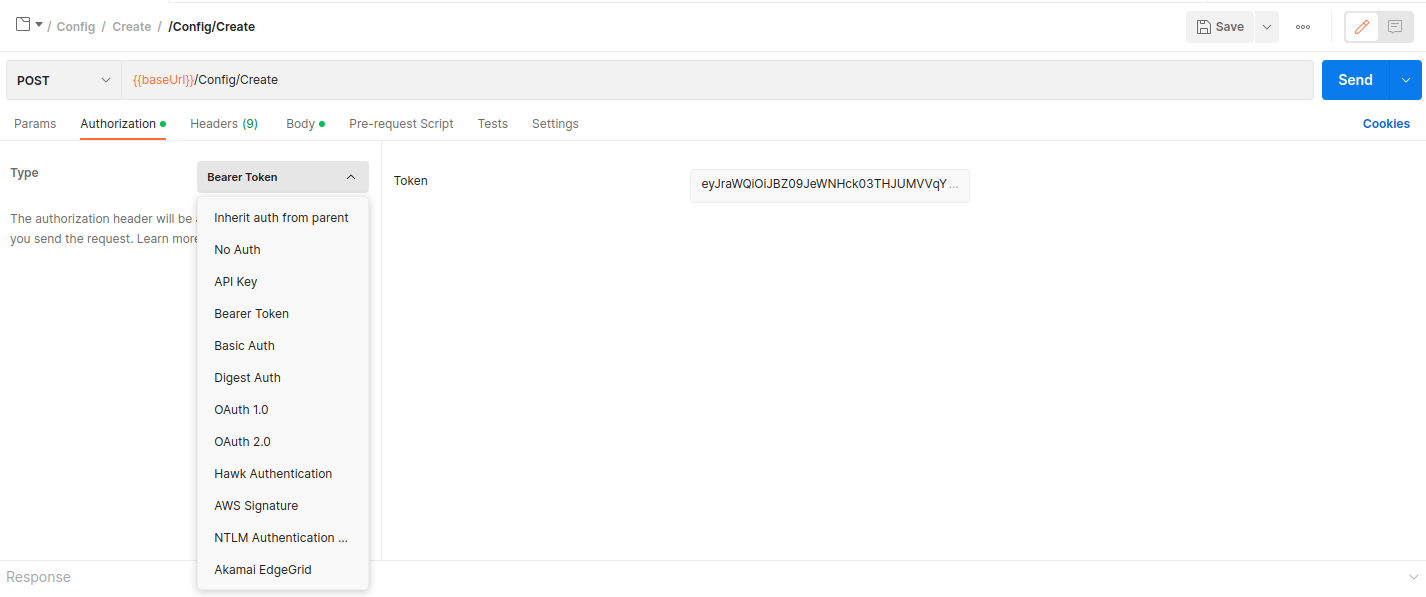
- Go to postman and paste token to Authorization > TYPE: Bearer Token >> [Token] ...
- For auth: UserLevel, need to send “targerUserId” in Params>Path Variables>
KEY: targetUserId
VALUE: <targetUserId>
Email use in web interface for get access token.
- basicUserA
- Email: success+basicUserTest@simulator.amazonses.com
- Password: Abc123456!
- verifiedUserA
- Email: success+verifiedUserTestA@simulator.amazonses.com
- Password: Abc123456!
- verifiedUserB
- Email: success+verifiedUserTestB@simulator.amazonses.com
- Password: Abc123456!
- superUserA
- Email: success+superUserTest@simulator.amazonses.com
- Password: Abc123456!
Authorizer
AppLevel
There is no “owner” for this level, users with application level permissions to administer roles can do so
- Can change other user roles.
- Can create new roles
- Change site-wide settings
- SuperUser permissions for lower level RBAC (eg: User level or Category level RBAC permissions)TODO: so, you all need to give the role permission to user)
allow the role permission to user appLevel
- SuperUser
- can do all actions:
- CREATE | UPDATE | DELETE | GET | LIST
- VerifiedUser
- can do some actions:
- CREATE | GET | LIST
- BasicUser
- can do few actions:
- GET
example reloPermission
- AppLevel:superUser
{
"roleIdKey":"AppLevel_this-is-uuid-for-role-superUserA",
"service_resource_action":"ServiceTemplate_Config_Create",
"permission": "accept"
}
- AppLevel:verifiedUser
{
"roleIdKey": "AppLevel_this-is-uuid-for-role-verifiedUserA",
"service_resource_action": "ServiceTemplate_Config_Create",
"permission": "accept"
}
- AppLevel:basicUser
{
"roleIdKey": "AppLevel_this-is-uuid-for-role-basicUserA",
"service_resource_action": "UserAccountAppLevel_UserRole_Get",
"permission": "accept"
}
example UserRoles
- AppLevel:superUser
{
"userId": "this-is-uuid-for-user-superUserA",
"roleIdKey": "AppLevel_this-is-uuid-for-role-superUserA"
}
- AppLevel:verifiedUser
{
"userId": "this-is-uuid-for-user-verifiedUserA",
"roleIdKey": "AppLevel_this-is-uuid-for-role-verifiedUserA"
}
- AppLevel:basicUser
{
"userId": "this-is-uuid-for-user-basicUserA",
"roleIdKey": "AppLevel_this-is-uuid-for-role-basicUserA"
}
setting for authorizer appLevel
- function.yml
- For LambdaFunctionHdrApi applevel
LambdaFunctionHdrApi:
events:
- http:
path: Lambda/LambdaAction
method: post
cors: true
authorizer:
arn: ${self:custom.iz_authorizerAppLevel}
type request
resultTtlInSeconds: 0
UserLevel
- All permissions are linked to one user id.
- Has an owner (the current user), that user always has full permissions for their user id.
- Available roles are shared by all users, any user can create new roles and add permissions, roles can then be used by any users.
- Only the creator of the role can make changes later (for the start - in future we can add RBAC management of user level roles).
example permissions:
- Can administer users roles/permissions
- Can administer sell offers for this user
allow the role permission to user
example rolePermission
- Create role permission, user can do action, can create in seed data or run from
https://us-east-2.console.aws.amazon.com/apigateway/home?region=us-east-2#/apis/rwnhg855jd/resources/y8erkk : RolePermissionCreateHdrApi
- UserLevel:verifiedUser
{ "roleIdKey":"UserLevel_this-is-uuid-for-role-verifiedUserA_this-is-uuid-for-role-verifiedUserB", "service_resource_action":"VariantStandard_Product_AddProduct", "permission": "accept" }
example userRoles
- Create userRoles, user have role, can create from
- UserLevel:verifiedUser
{ "userId": "this-is-uuid-for-user-verifiedUserB", "roleIdKey": "UserLevel_this-is-uuid-for-user-verifiedUserA_this-is-uuid-for-user-verifiedUserB" }
setting for authorizer userLevel
- function.yml
- For LambdaFunctionHdrApi userlevel, need to add adds targetid to api route/path
LambdaFunctionHdrApi:
events:
- http:
path: Lambda/LambdaAction${self:custom.api_path_targetid_suffix}
method: post
cors: true
authorizer:
arn: ${self:custom.iz_authorizerUserLevel}
type request
resultTtlInSeconds: 0
Test API in post man
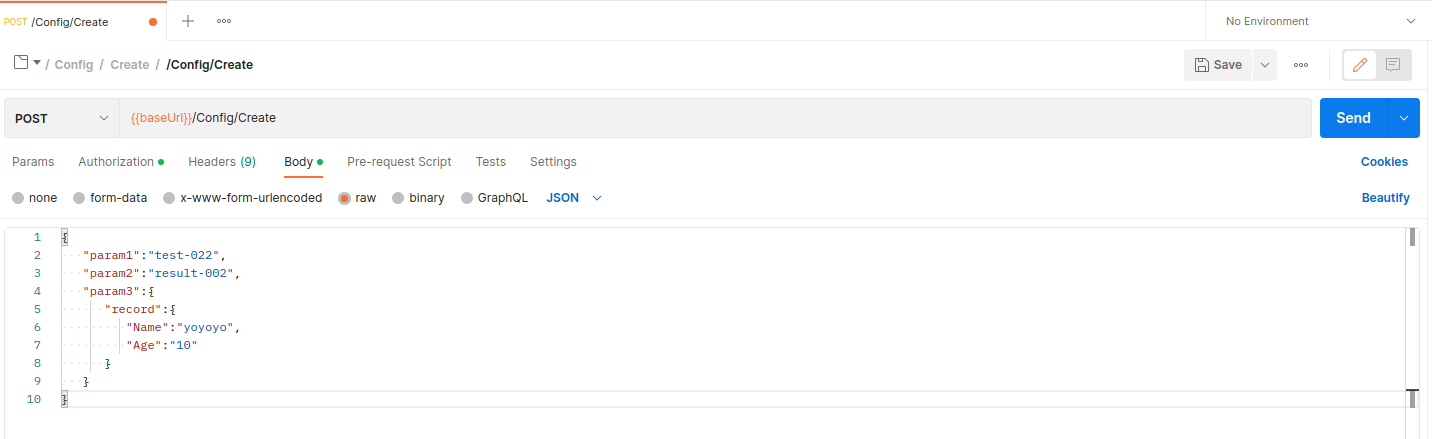
- Click on workspace and choose folder and file testing
- Click Body choose rew> JSON and push your request in code block.
- and send message.
- Below block show return response.
- If test api works . will show return response and status code: 200 OK
- You can see more response see in cloudwatch in function testing.